Just one day after reaching a net deposit of $60 billion, the decentralized lending protocol Aave became the target of a large-scale phishing campaign through the Google Ads platform.
On August 6th, Aave officially became the first DeFi protocol to reach a TVL of $60 billion, distributed across 14 different blockchains. This figure represents an impressive threefold increase compared to the same period last year, confirming Aave's leading position in the decentralized lending segment.
However, this success also attracted the attention of cybercrime groups. Just one day after the announcement, fake advertisements appeared on Google's search results page, luring users to access sophisticated malicious websites designed to mimic Aave's official interface.
According to a report from blockchain security company PeckShield, hackers exploited Google's advertising system to deploy malicious links aimed at deceiving Aave users. This incident reflects the increasing trend of attacks targeting large DeFi protocols with high liquidation and scale.
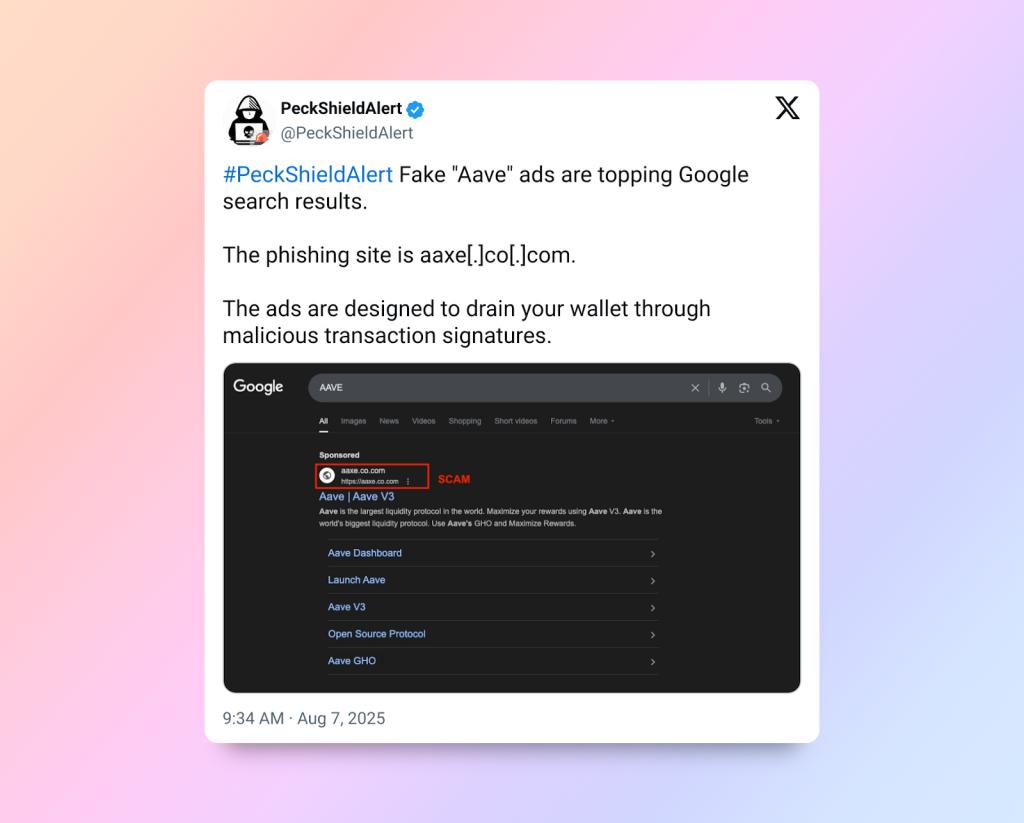
This phishing strategy exploits users' trust in reputable brands and the popularity of Google Search. When users click on the fake advertisement links, they are redirected to a website with an interface almost identical to the official Aave platform. Here, victims are asked to connect their cryptocurrency wallet and grant access to the fake application.
Once these permissions are granted, attackers can perform unauthorized transactions and withdraw all assets from the user's wallet. Due to the immutable nature of blockchain, these transactions can hardly be reversed. Although specific financial damage has not been disclosed, the use of Google Ads as a distribution channel indicates potential impact on a large number of potential users. This incident emphasizes the rule in the DeFi space: high scale and liquidation are directly proportional to the level of attraction from malicious actors.
Security experts recommend that users take proactive preventive measures. First, always thoroughly verify the URL address before making any transactions, prioritizing direct access instead of through advertisement links. Second, use access management tools like Revoke.cash to monitor and revoke permissions granted to decentralized applications.