Original | Odaily Odaily
Author | Ethan
Original title: UXLINK suffers a series of robberies: The hacker who issued 1 billion tokens just lost 500 million to a phishing gang
Another black swan moment has occurred, and this time the project that was hit is UXLINK, a star project in the Web 3 social track.
This project, which started in April 2023, is positioned as an on-chain social relationship and group network, and its highest market value once exceeded US$370 million.
From the sudden attack in the early morning to the hackers being tricked by anti-phishing, in just over 10 hours, UXLINK experienced the most chaotic moment in the history of the project:
More than $11.3 million in stolen assets;
The hacker is suspected of issuing an additional 1 billion tokens through the contract;
6732 ETH (approximately $28.1 million) was cashed out on the chain;
The token plummeted, with the intraday drop exceeding 80% at one point.
What’s even more outrageous is that this hacking incident had a “secondary plot reversal”: the hackers had just swindled tens of millions of dollars in assets from the agreement, but 542 million tokens were suspected to have been stolen by a phishing gang, which became a famous “black eating black” scene.
Below, Odaily will sort out the events and use a timeline to string together the important nodes from this storm to the present.
Attack breaks out: Multi-sig breached, funds transferred
At 00:43 on September 23rd, Cyvers Alerts first disclosed that an attacker executed a delegateCall operation on the UXLINK multi-sig wallet at 22:53 on September 22nd, deleting the existing administrator role and setting themselves as the sole controller. Subsequently, they called addOwnerWithThreshold to quickly authorize and transfer a series of assets: 4 million USDT, 500,000 USDC, 3.7 WBTC, 25 ETH, and approximately 3 million UXLINK were transferred out and partially bridged to the mainnet. Almost all of the stablecoins were converted to DAI.
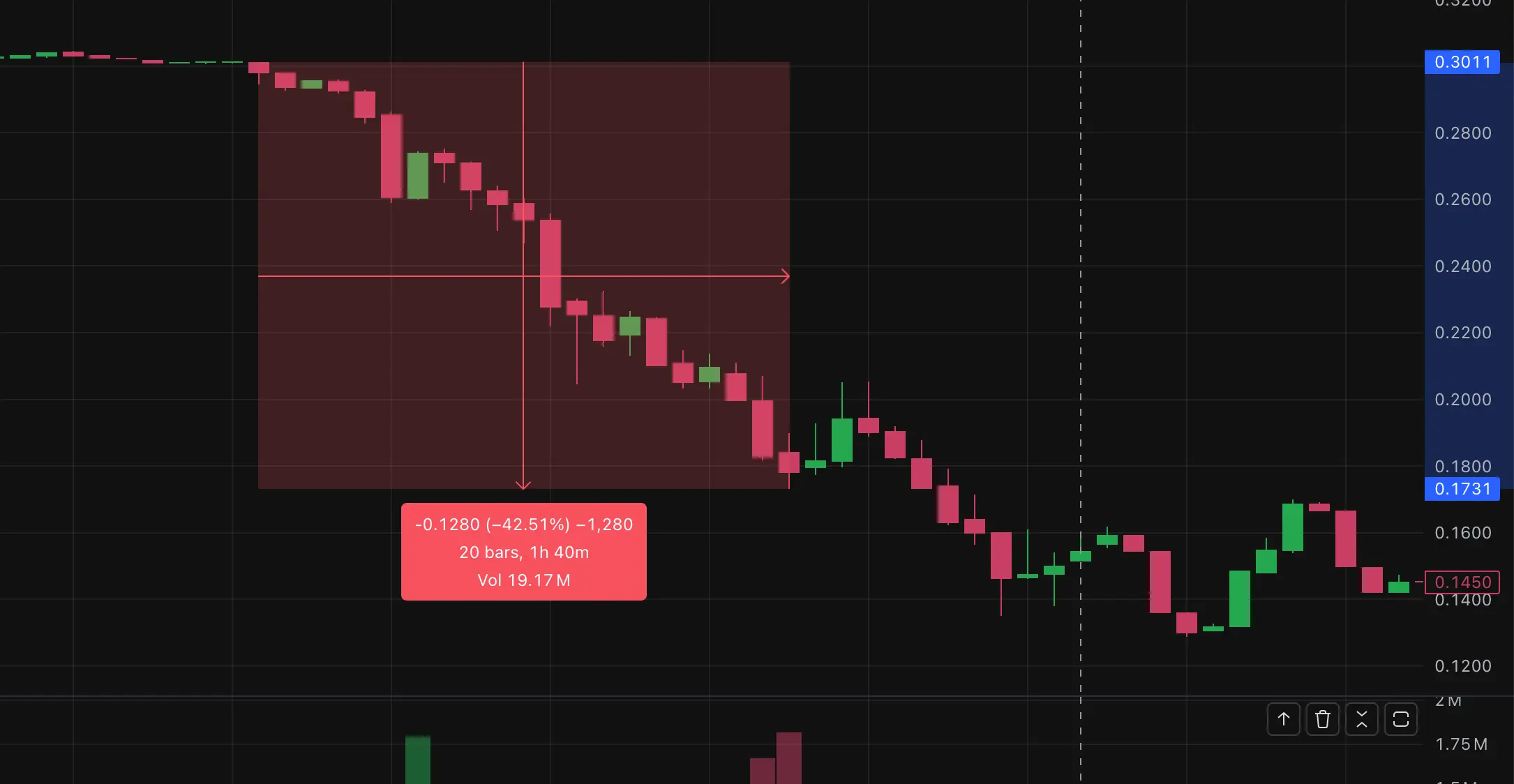
Just five minutes later, the market experienced a dramatic shock. UXLINK's spot price plummeted below 0.18 USDT, reaching a low of 0.1731 USDT, a 24-hour drop of 45.87%. The amount of liquidated positions also rapidly increased, reaching over $5.5 million across the network, including $3.68 million in long positions, further exacerbating the panic.
Official response: Emergency freeze, transparent disclosure
At 1:40 a.m. on September 23, UXLINK officially responded for the first time, admitting that it had been attacked, saying, "We are coordinating with multiple exchanges to freeze funds, and have contacted security experts and police to intervene."
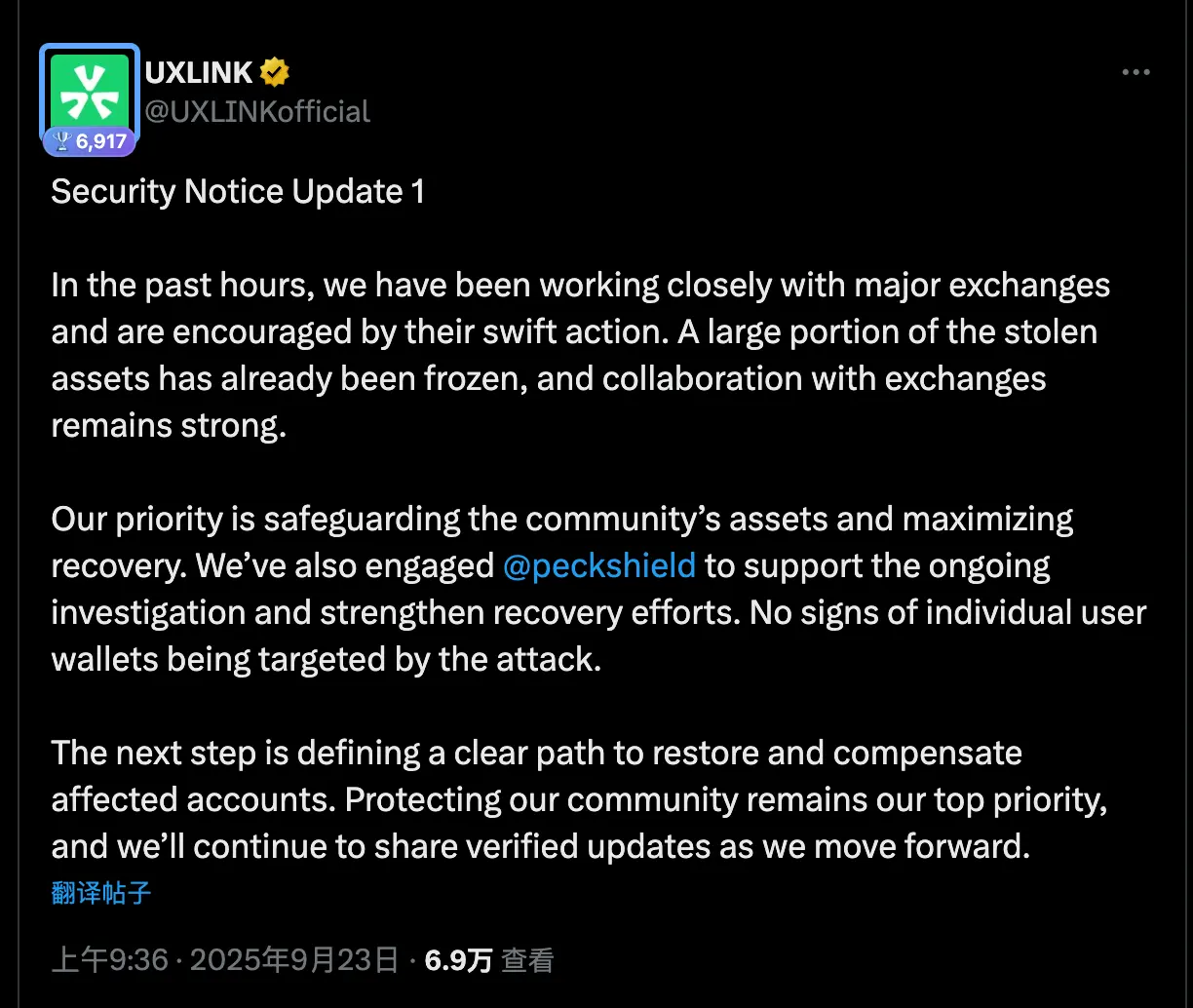
At 9:38 AM, officials announced another announcement: "Most of the stolen assets have been successfully frozen." The team confirmed that PeckShield had intervened to track the stolen assets and emphasized that there was no indication of personal wallet damage. A compensation and reimbursement mechanism would be developed later. The announcement repeatedly emphasized that "protecting community assets is the top priority."
Escalating situation: Hackers issue 1 billion additional tokens, causing on-chain price to plummet
Based on the lessons learned from other projects, the hacker succeeded, the project was saved, and the story was basically coming to an end, but the hacker did not stop there.
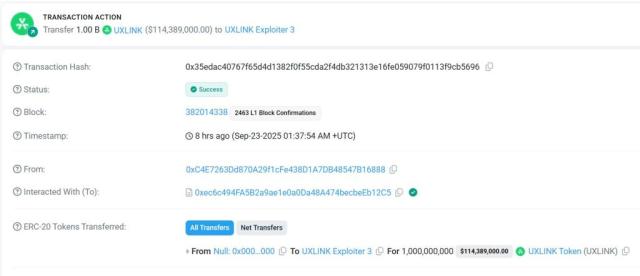
At 9:54 AM on September 23rd, according to on-chain data, an attacker successfully minted 1 billion UXLINK tokens (transaction hash: 0x35edac…5696) through the contract's minting function and transferred them to the address 0xeff9CE…b8b7eB9a7. (This address had previously been distributing newly minted UXLINK tokens, and has now completed its distribution.)
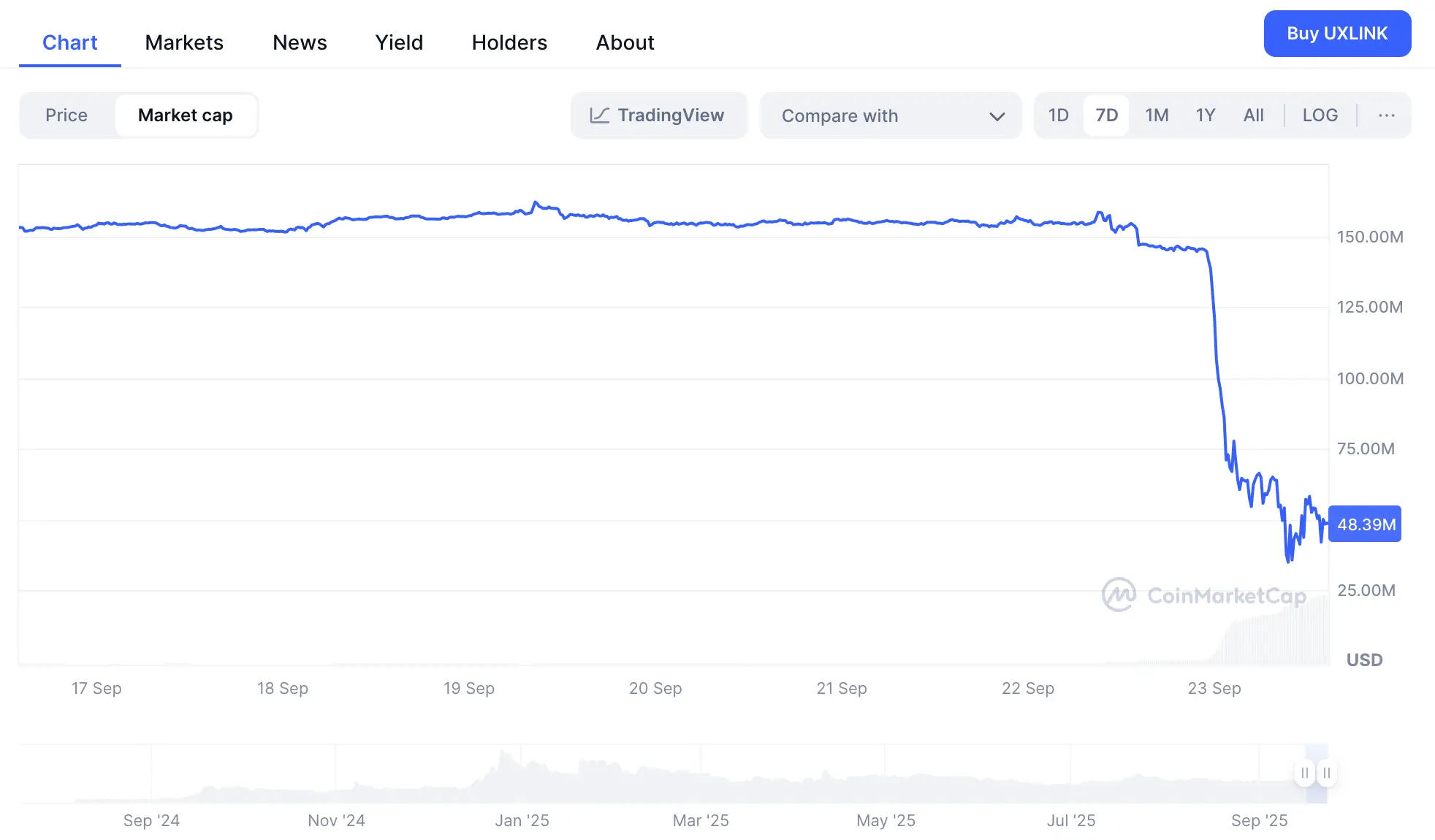
UXLINK's futures price quickly plummeted to below $0.056, with the largest intraday drop exceeding 80%. A significant price gap emerged between on-chain spot prices and CEX prices, prompting major exchanges like OKX and Bybit to temporarily delist the UXLINK trading pair. According to CoinMarketCap, the project's market capitalization plummeted from $150 million the previous day to less than $50 million.
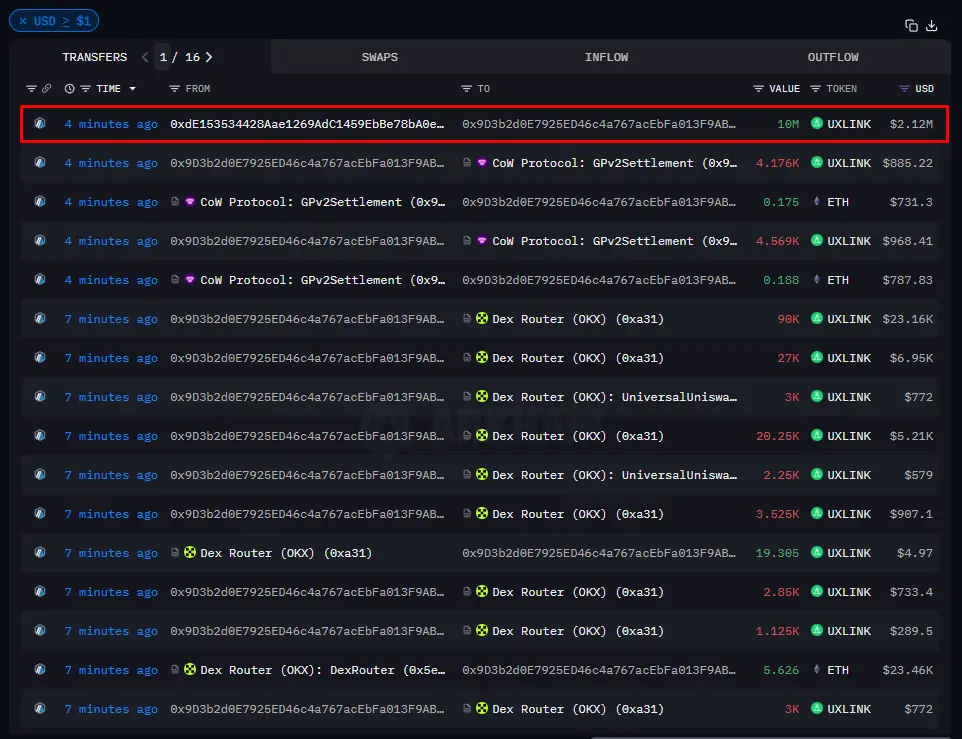
An hour later, UXLINK officially confirmed the issuance, stating that it constituted a serious violation of the whitepaper, causing further market panic and devastating price fluctuations in the liquidity pool. The team also issued an urgent notice urging users to temporarily refrain from trading tokens on DEXs and planned to implement a token swap program in an attempt to restructure the economic system devastated by the issuance.
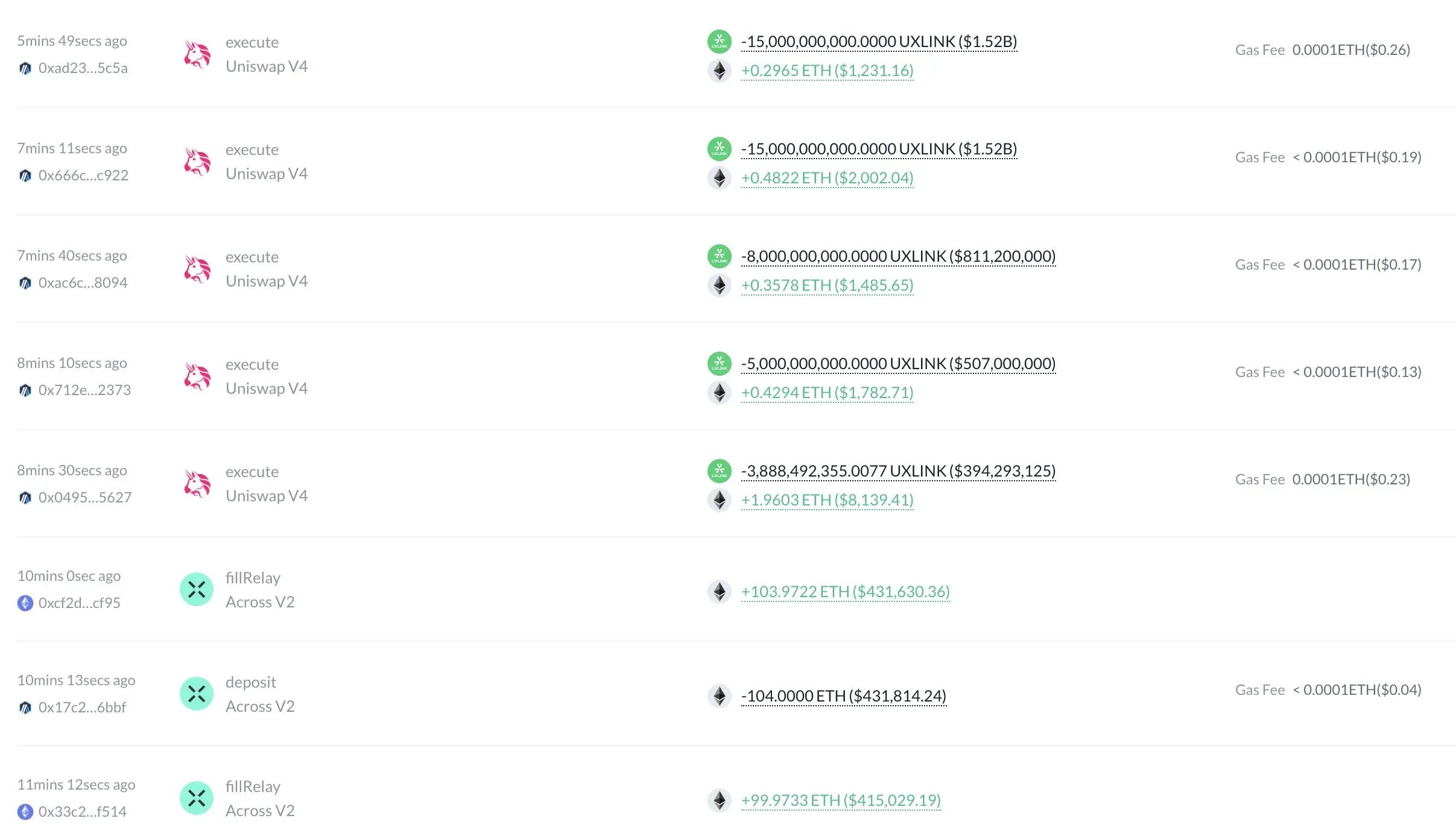
Hacker liquidation: cashed out 6732 ETH
According to Lookonchain, the attacker did not stop at simply issuing additional UXLINK. He transferred a large amount of UXLINK to multiple addresses and quickly liquidated them on a decentralized exchange (DEX), accumulating 6,732 ETH (approximately $28.1 million). He also allegedly transferred some of the funds to a centralized exchange (CEX) for further withdrawals.
Furthermore, there was widespread speculation within the community, with some suggesting that "this might be a privilege leak caused by internal conflicts within the team," and others even alluding to the "bribery network exposed three days ago." However, this claim is currently mere speculation and has yet to be confirmed by reliable evidence.
Secondary reversal: Hackers also phished
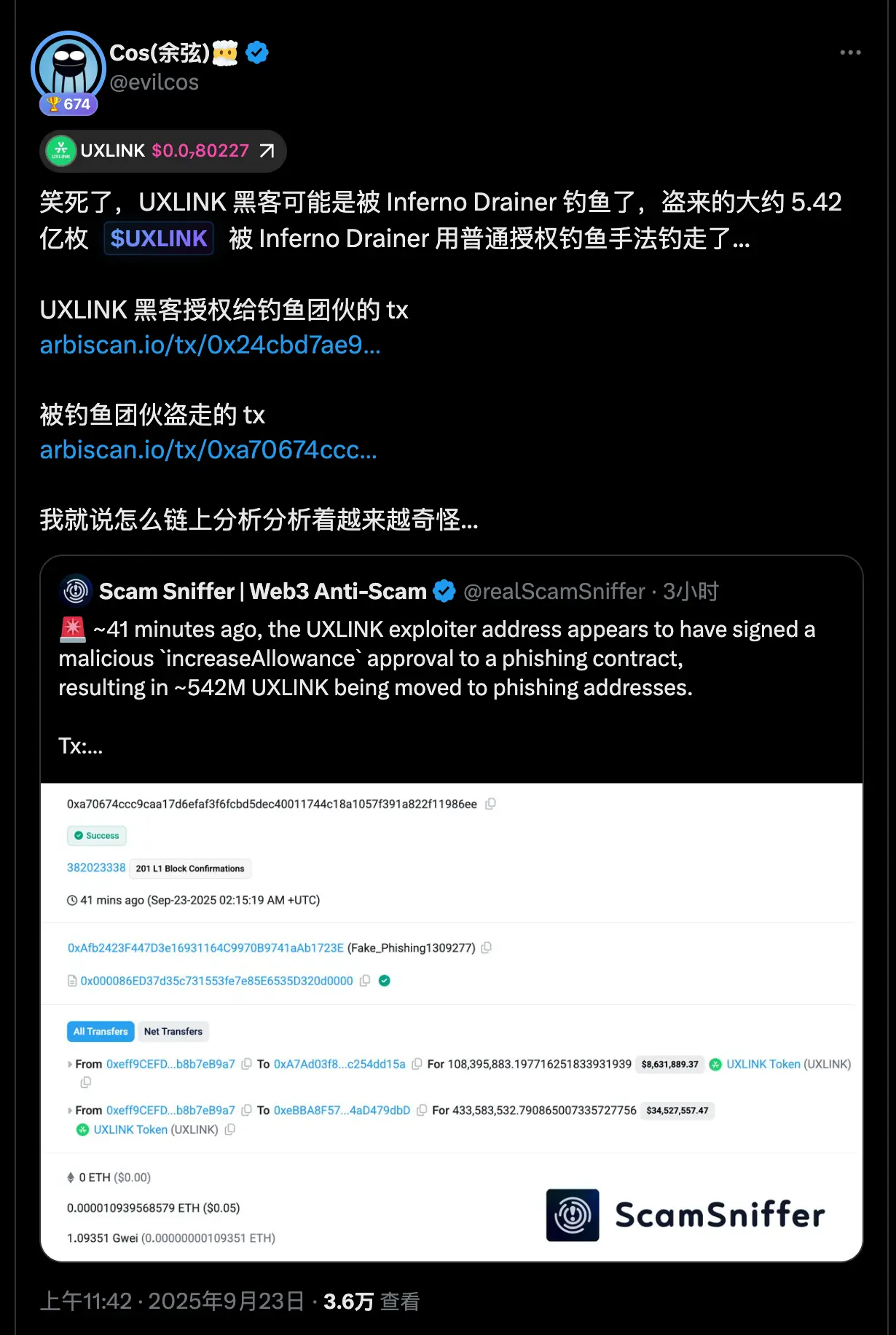
The story doesn't end here. At 11:43 AM, security researcher Yu Xian (@evilcos) posted a post revealing that the UXLINK hackers were suspected of falling into the Inferno Drainer phishing scam during their operations, and were robbed of approximately 542 million UXLINK tokens through a "normal authorization" method.
Yu Xian posted two transaction hashes as evidence in the article, and jokingly said: "I was wondering why the on-chain analysis was getting more and more weird..." This reversal added drama to the already chaotic situation and quickly sparked heated discussions in the community.
Project owner: Stabilize emotions and promise compensation
The event coincided with the 2025 Korea Blockchain Week KBW (September 22-28, 2025), which is also one of the more influential blockchain events in Asia.
The picture below is a picture shared by netizens of UXLINK's booth at the event (if nothing unexpected happens, this booth should be packed):

Throughout the incident, the UXLINK team continued to release announcements in the official TG group in an attempt to reassure investors. The latest announcement stated, "We will not be defeated. Instead, we will emerge stronger and more united. KBW and Season 5 activities are still moving forward."
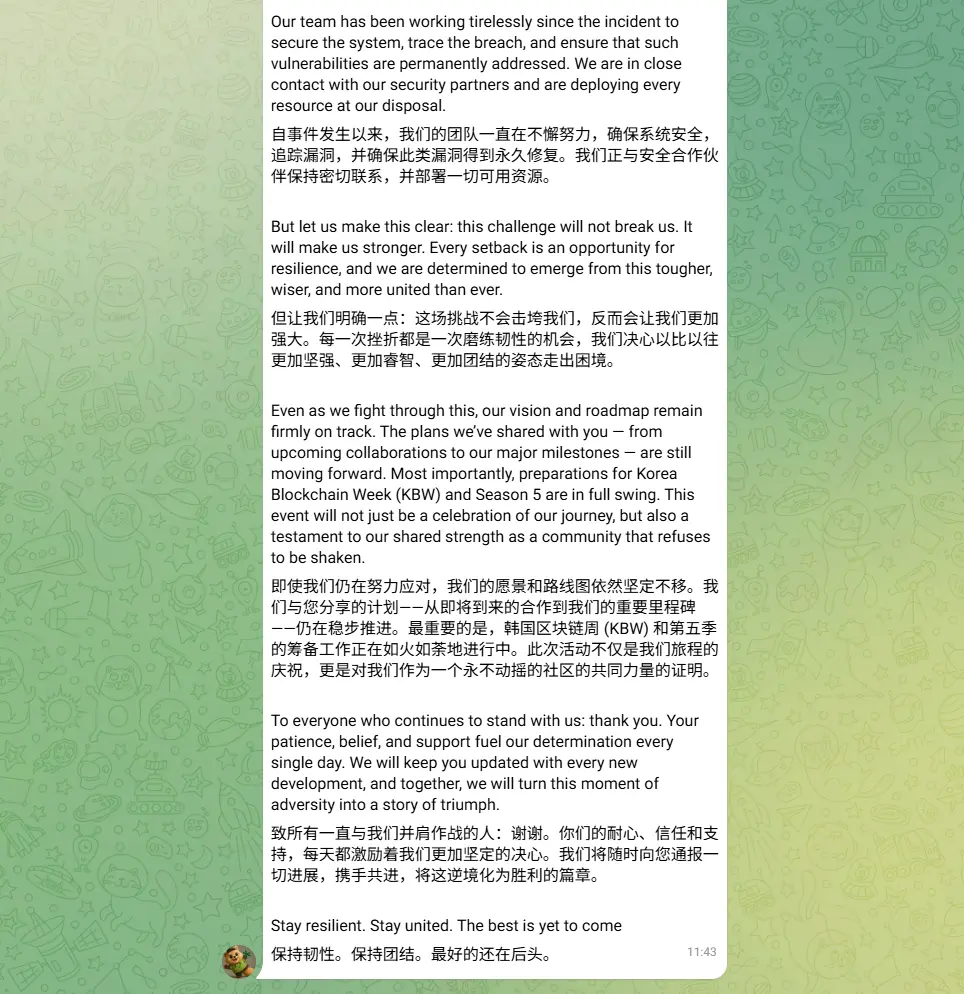
In addition, the team also confirmed that it has contacted several centralized exchanges to suspend UXLINK trading in order to carry out subsequent token swaps and compensation plans.
Community buy the dips, isn't it fun (or miserable)?
The bigger the waves, the bigger the fish... Many people chose to "buy the dips" during this hacker attack, but due to the twists and turns of the incident, most of the buy the dips were wasted.
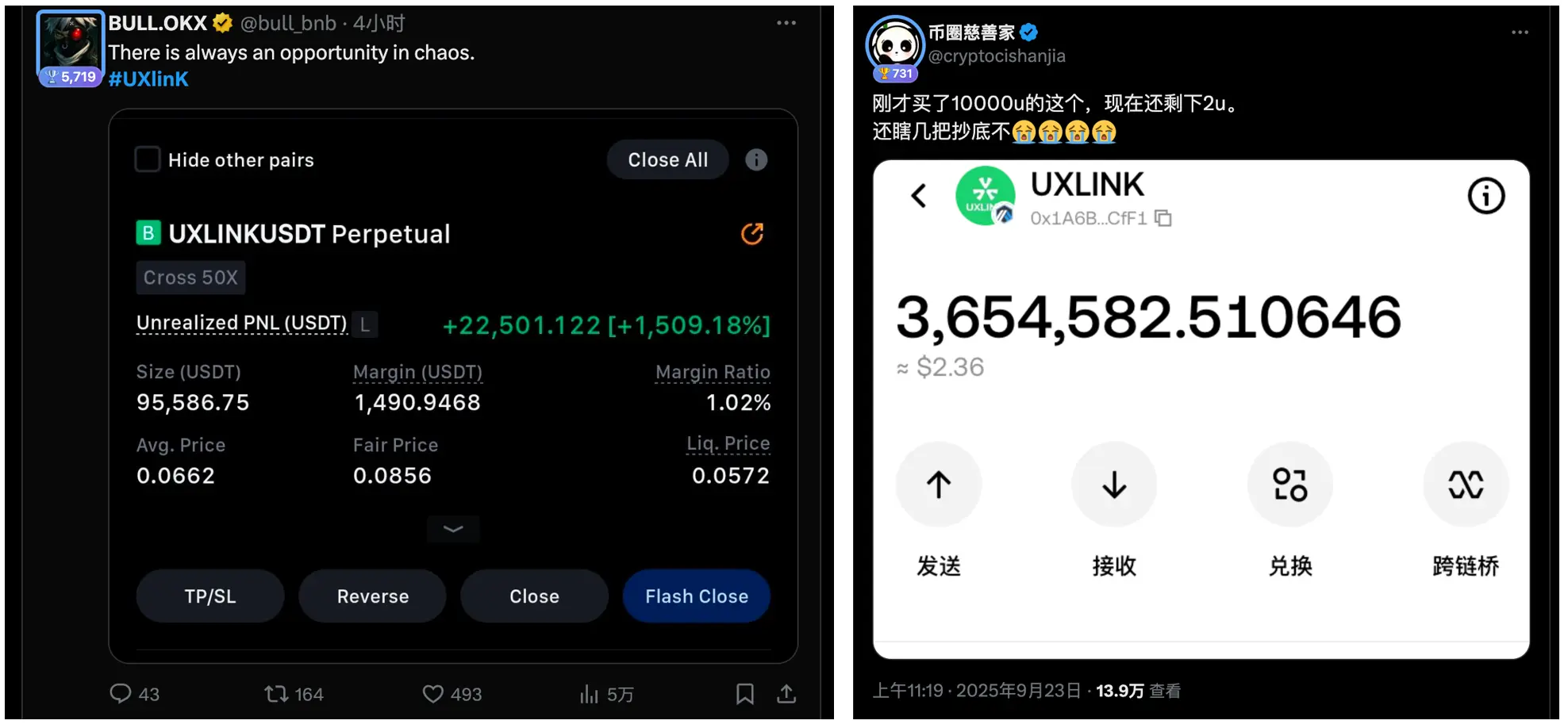
Odaily would like to remind you that the full picture of the attack has not yet been clearly revealed, and the situation is still shrouded in mystery. SocialFi products often have loosely linked prices to fundamentals, and any current operations will result in significant uncertainty. Act with caution and DYOR.
Whether UXLINK's compensation plan can rebuild trust and its roadmap can be smoothly implemented will be key to the project's ability to recover from its current predicament. Odaily will continue to monitor and report on its latest developments.
Twitter: https://twitter.com/BitpushNewsCN
BitPush TG discussion group: https://t.me/BitPushCommunity
Bitpush TG subscription: https://t.me/bitpush